FAT stores local times
NTFS stores UTC times
UTC == Coordinated Universal Time - a successor to GMT
GMT == Greenwich Mean Time, absolute time reference and doesn't change with the seasons
Summer Time == Daylight Saving Time
Winter Time == Standard Time
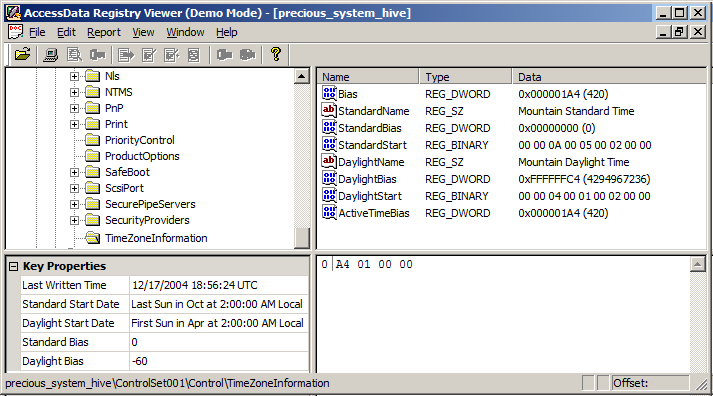
Time Zone Info:
-
StandardName: time zone name
-
StandardStart: month, week, day, and time of day when the transition from daylight saving time to standard time occurs. Usually Oct/Nov
-
StandardBias: usually zero; the bias in munutes during standard time period. Can be ignored.
-
Bias: the current time zone offset from GMT, interpreted as GMT-Bias (minutes). This is the difference between GMT and current local time.
-
ActiveTimeBias: time zone offset from GMT including DaylightBias, interpreted as GMT-ActiveTimeBias (minutes)
Daylight Saving Time Info:
-
DaylightName: daylight saving time description, e.g. "PDT", Pacific Daylight Time
-
DaylightStart: month, week, day, and time of day when the transition from standard time to daylight saving time occurs.. Usually Mar/Apr
-
DaylightBias: offset in minutes added Bias to form the current bias during daylight saving time. Usually -60.