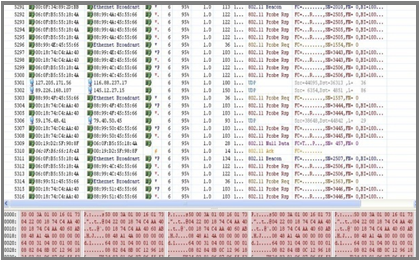
Raw Forensics: manual log review
| <<< Wireless Vulnerability Assessment, cont. | Index | Evolution of Wireless Forensics Methods, cont. >>> |

Raw Forensics: manual log review
| <<< Wireless Vulnerability Assessment, cont. | Index | Evolution of Wireless Forensics Methods, cont. >>> |