
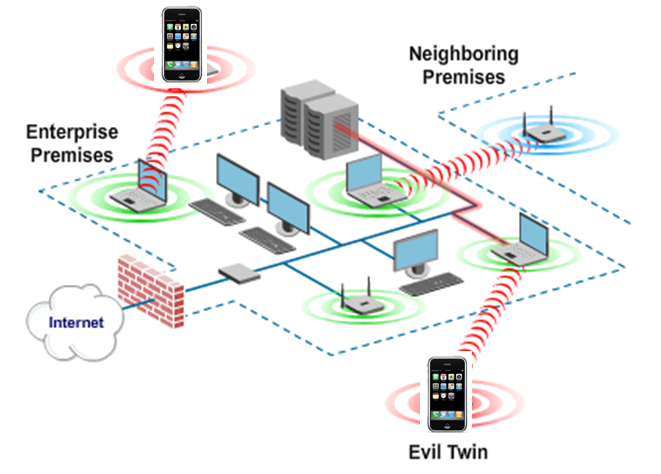
Wi-Fi users bypassing enterprise security through Smart Phone hotspots
| <<< Smart Phone Vulnerabilities | Index | Requirements for Network Forensics >>> |


Wi-Fi users bypassing enterprise security through Smart Phone hotspots
| <<< Smart Phone Vulnerabilities | Index | Requirements for Network Forensics >>> |