-
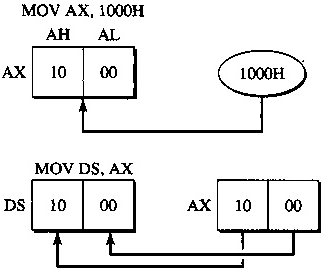
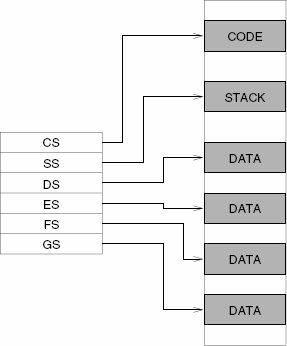
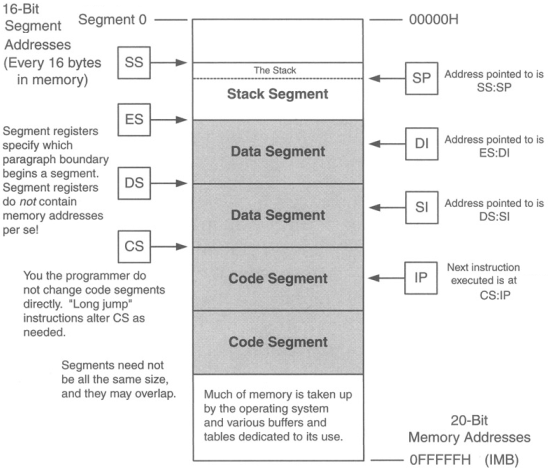
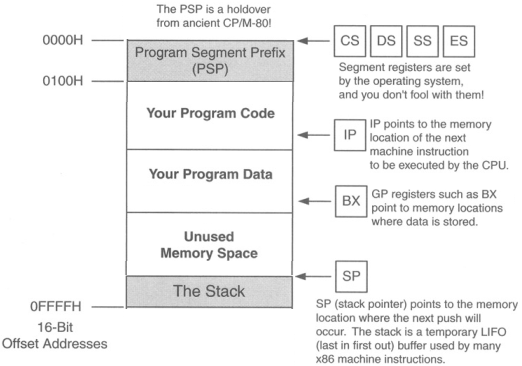
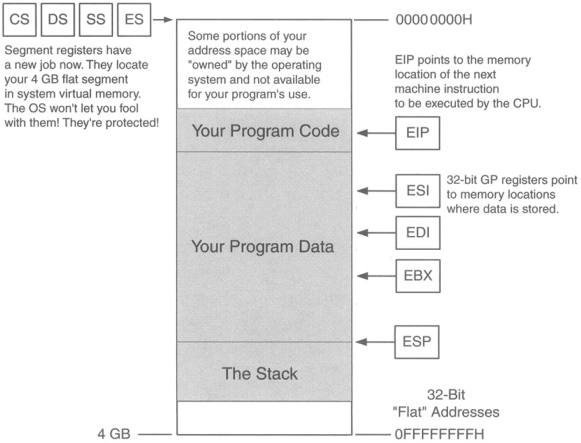
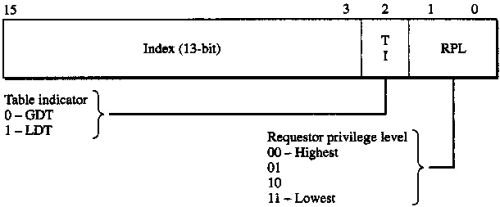
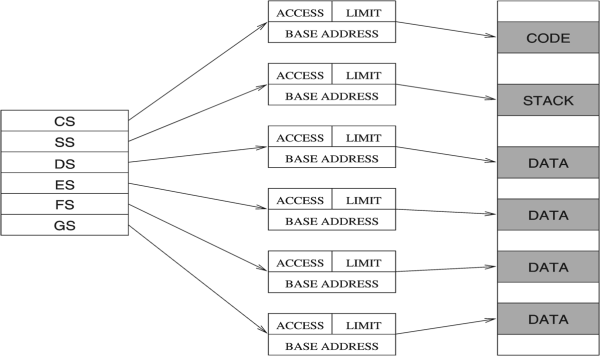
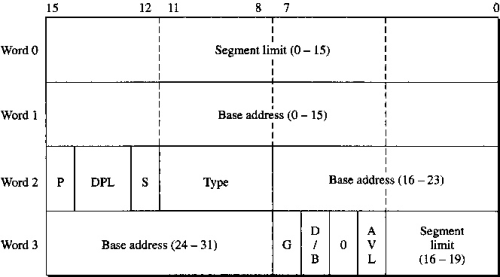
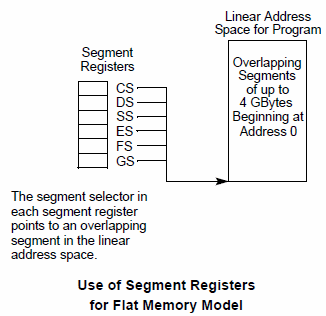
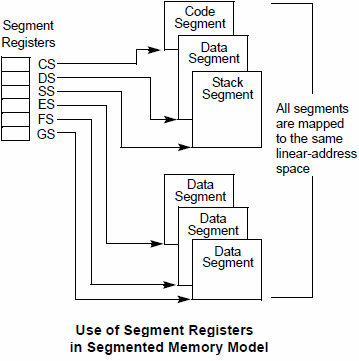
Segment registers are basically memory pointers located inside the CPU.
-
Segment registers point to a place in memory where one of the following things begin:
-
Data storage
-
Code execution.
-
-
-
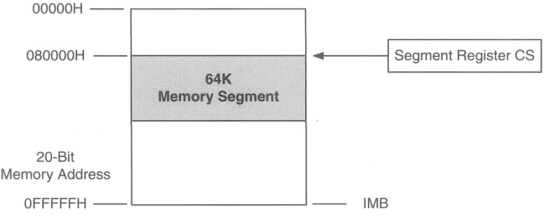
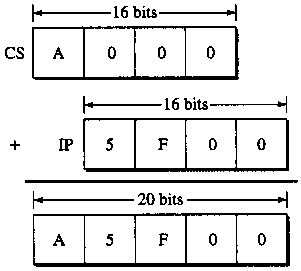
Example: code segment register CS points to a 64K region of memory: